Security In The Cloud Ensuring Robust Protection For Your Online Data

Hybrid Cloud Security 5 Key Steps To Securing Cloud Environments Customer Centric Product What is cloud data security? cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: ensuring the security and privacy of data. Cloud computing and analytics enable organizations to make data driven decisions. according to the global idc survey data: 83% of ceos want a data driven organization. 74% of senior executives require data in decision making. organizations need to protect sensitive information to ensure the integrity of the data that their analytics models use.
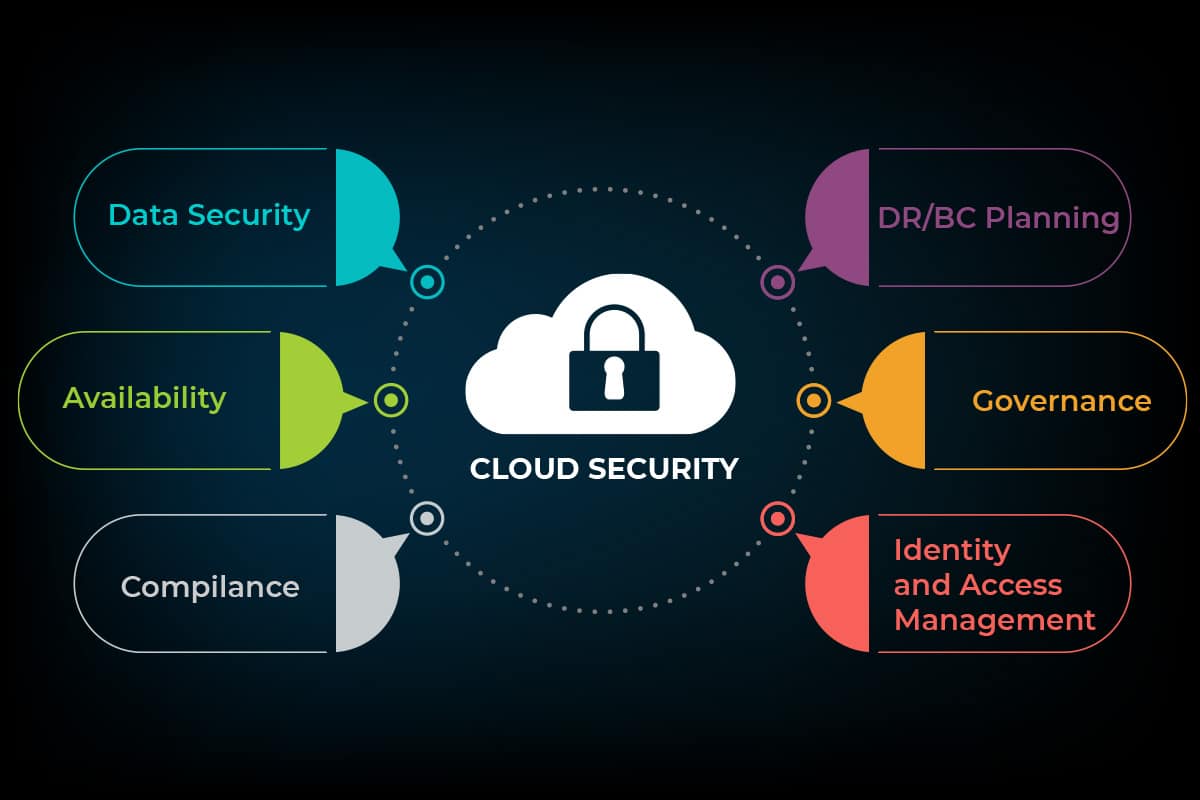
Cloud Security Understanding The Shared Responsibility Model Layots Technologies Therefore, it is crucial to implement best practices to secure data in cloud services. 1. choose a reliable cloud service provider. choosing a reputable cloud service provider is the first step toward securing data. the provider should offer secure data storage, encryption, and access controls. 13. encrypt your data. cloud data encryption is key to a robust cloud security strategy. it allows for a seamless and secure flow of data among cloud based applications by concealing it from unauthorized users. data should be encrypted in the cloud itself and when it is in transit to ensure optimal protection. Utilize dspm: use dspm (data security posture management) to continuously assess and enhance your data security measures in the cloud, ensuring robust protection. encrypt data: make it unreadable without a key. restrict access: use passwords, two factor authentication, and other methods. 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to.

Cloud Erp Security Plex Utilize dspm: use dspm (data security posture management) to continuously assess and enhance your data security measures in the cloud, ensuring robust protection. encrypt data: make it unreadable without a key. restrict access: use passwords, two factor authentication, and other methods. 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to. And as a business’s public cloud footprint grows in size and complexity, so does the need for cloud data security. cloud data security refers to the technologies, services, policies, and processes that protect sensitive data and other digital assets—within, across, and outside of clouds. it helps ensure that assets remain safe from security. The role of the cloud management plane. the management plane serves as a critical interface, centralizing the control of cloud resources. this plane allows management through apis and web consoles instead of physical hardware. this improves efficiency but introduces new security challenges. ensuring robust security controls is crucial as access.

Protecting Your Data In The Cloud The Ultimate Guide To Cloud Security Threats And Solutions And as a business’s public cloud footprint grows in size and complexity, so does the need for cloud data security. cloud data security refers to the technologies, services, policies, and processes that protect sensitive data and other digital assets—within, across, and outside of clouds. it helps ensure that assets remain safe from security. The role of the cloud management plane. the management plane serves as a critical interface, centralizing the control of cloud resources. this plane allows management through apis and web consoles instead of physical hardware. this improves efficiency but introduces new security challenges. ensuring robust security controls is crucial as access.
Cloud Security Best Practices Protecting Your Data Skillfloor

Comments are closed.