Safeguarding Your Data Best Practices For Secure Cloud Storage

Safeguarding Your Data Best Practices For Secure Cloud Storage Ensure that your employees are aware of the security risks associated with storing data in cloud services and are trained on best practices for securing data. this includes regular security awareness training and policies for reporting suspicious activity. 11. implement principles of zero trust. zero trust is a security strategy. Cloud security: best practices for enterprise cloud storage solutions. when it comes to storing critical business data in the cloud, security should always be a top priority. with the increasing number of cyber attacks and data breaches, it’s essential to implement strong security measures to protect your enterprise cloud storage solutions.
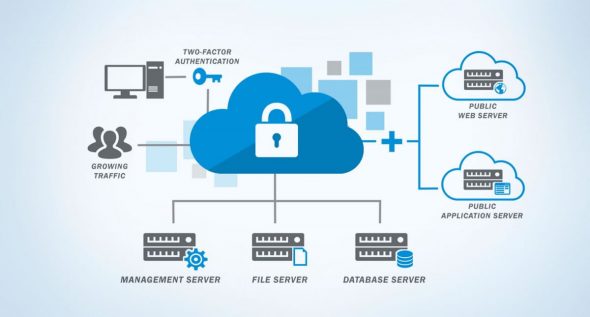
Cloud Storage Security Best Practices Best practices for securing your data with cloud storage securing enterprise storage data requires planning ahead to protect your data from future threats and new challenges. beyond the fundamentals, cloud storage offers several security features, such as uniform bucket level access, service account hmac keys, iam conditions, delegation tokens. Cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: the cloud data protection and security strategy must also protect data of. Cloud storage security includes technologies and practices businesses use to protect their data in cloud storage solutions. this can consist of safeguards against theft, deletion, unauthorized access, or file corruption. some security issues are the same between cloud storage and on premises frameworks. however, moving to a new environment can. Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach.

Cloud Security Best Practices Safeguarding Your Data Cloud storage security includes technologies and practices businesses use to protect their data in cloud storage solutions. this can consist of safeguards against theft, deletion, unauthorized access, or file corruption. some security issues are the same between cloud storage and on premises frameworks. however, moving to a new environment can. Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach. The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 5. secure your data with vpc service controls with vpc service controls, you can configure security perimeters around the resources of your cloud storage service and control exfiltration of data across the perimeter boundary. for example, a vm within a vpc network that is part of the service perimeter can read from write to a cloud storage bucket.

Cloud Security 101 Safeguarding Your Data In The Cloud Cloud Computing The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 5. secure your data with vpc service controls with vpc service controls, you can configure security perimeters around the resources of your cloud storage service and control exfiltration of data across the perimeter boundary. for example, a vm within a vpc network that is part of the service perimeter can read from write to a cloud storage bucket.

Comments are closed.