Humans And Data Dont Mix Best Practices To Secure Your Cloud

Humans And Data Don T Mix Best Practices To Secure Your Cloud Youtube Stephen schmidt, aws ciso, will share hard earned lessons around potential gaps in your security plan, along with steps to lessen potential angles of attack.learning objectives:1: learn how to put a plan in place that takes advantage of pattern recognition.2: discover how to consider your own security blind spots with ways to self audit.3: see. The risk of humans touching sensitive data is clear, so how do you get them away from your data while also speeding up time to detection and remediation? stephen schmidt, aws ciso, will share hard earned lessons around potential opportunities in your security program, along with practical steps to improve the agility of your organization.

Aws Security Week Humans Data Don T Mix Best Practices To Secure Your Cloud Ppt Humans and data don’t mix: best practices to secure your cloud 1. session id: #rsac stephen schmidt humans and data don’t mix: best practices to secure your cloud csv t08 vice president and chief information security officer amazon web services (aws) @awssecurityinfo. 10. train your employees. ensure that your employees are aware of the security risks associated with storing data in cloud services and are trained on best practices for securing data. this includes regular security awareness training and policies for reporting suspicious activity. 11. Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach. Cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: the cloud data protection and security strategy must also protect data of.

Cloud Security Best Practices Protecting Your Data In The Cloud Be Learn Cloud Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach. Cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: the cloud data protection and security strategy must also protect data of. The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. Data accessibility: cloud data protection ensures corporate and customer data is not only safe but organized, managed, and highly accessible for users. this data accessibility is particularly important for companies with remote or mobile workforces. reputation management: a strong cloud data protection strategy can boost a company's reputation.

Infographic Best Practices For Securing The Cloud The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. Data accessibility: cloud data protection ensures corporate and customer data is not only safe but organized, managed, and highly accessible for users. this data accessibility is particularly important for companies with remote or mobile workforces. reputation management: a strong cloud data protection strategy can boost a company's reputation.
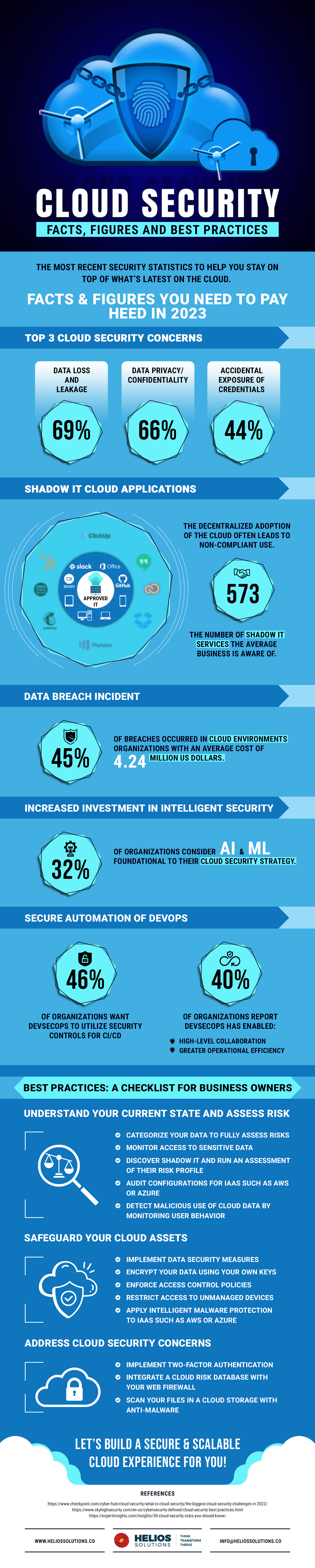
Securing Your Cloud Key Statistics And Best Practices Infographic

Comments are closed.