Cloud Security Threats Prevention Methods Best Practices
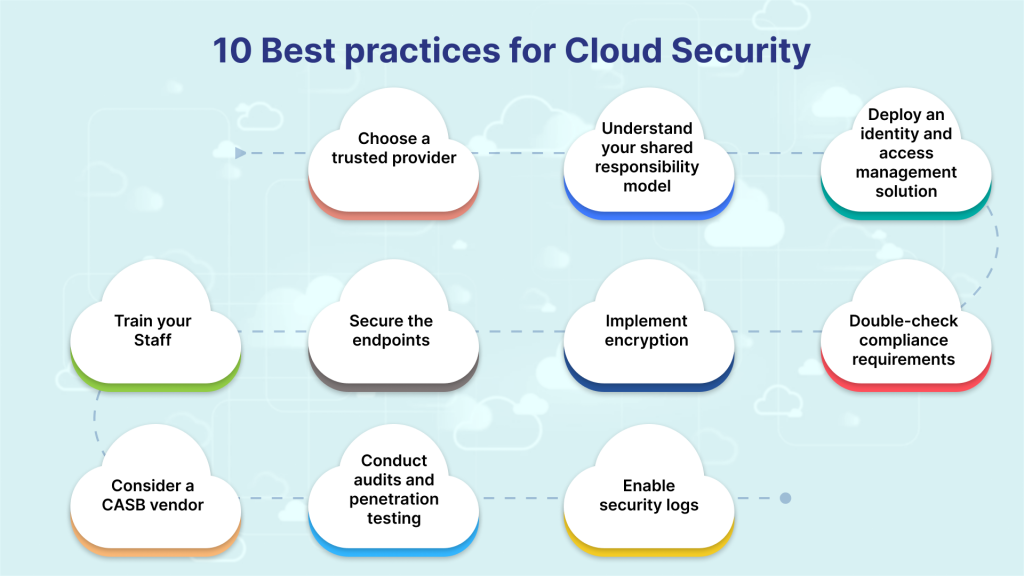
Cloud Security Threats Prevention Methods Best Practices Secure the perimeter. monitor for misconfigurations. use identity and access management. enable security posture visibility. implement cloud security policies. secure your containers. perform vulnerability assessment and remediation. implement a zero trust approach. implement a cybersecurity training program. Cloud security threats, prevention methods & best practices in 2024. the cloud computing market continues to grow and the global cloud computing market size was estimated at usd 602.31 billion in 2023 and is expected to grow at a cagr of 21.2% from 2024 to 2030, as per grand view research. aws, azure, and google currently dominate the market.
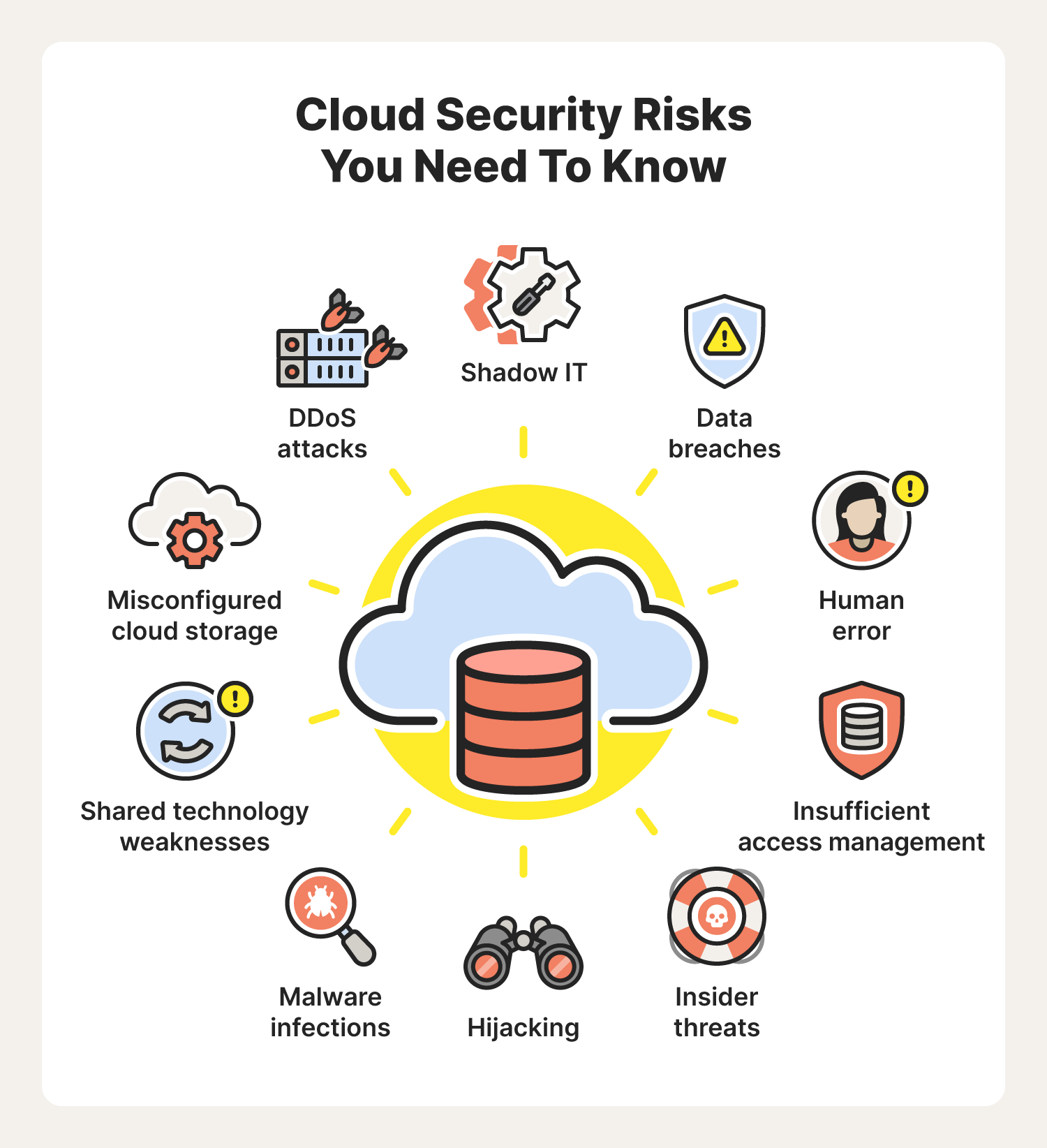
23 Cloud Security Risks Threats And Best Practices Norton The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 23 cloud security risks, threats, and best practices to follow. cloud security risks include data breaches, insufficient access management, malware infections, and more. learn how to better protect your data in the cloud. written by clare stouffer. published: july 11, 2023 7 min read. 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to. Data breaches. data losses. attack surface. insecure apis. misconfiguration. restricted visibility of cloud usage. contract breaches with business partners. hijacking of accounts. data breaches transpire when nefarious actors manage to penetrate the system and gain unauthorized access to sensitive data.

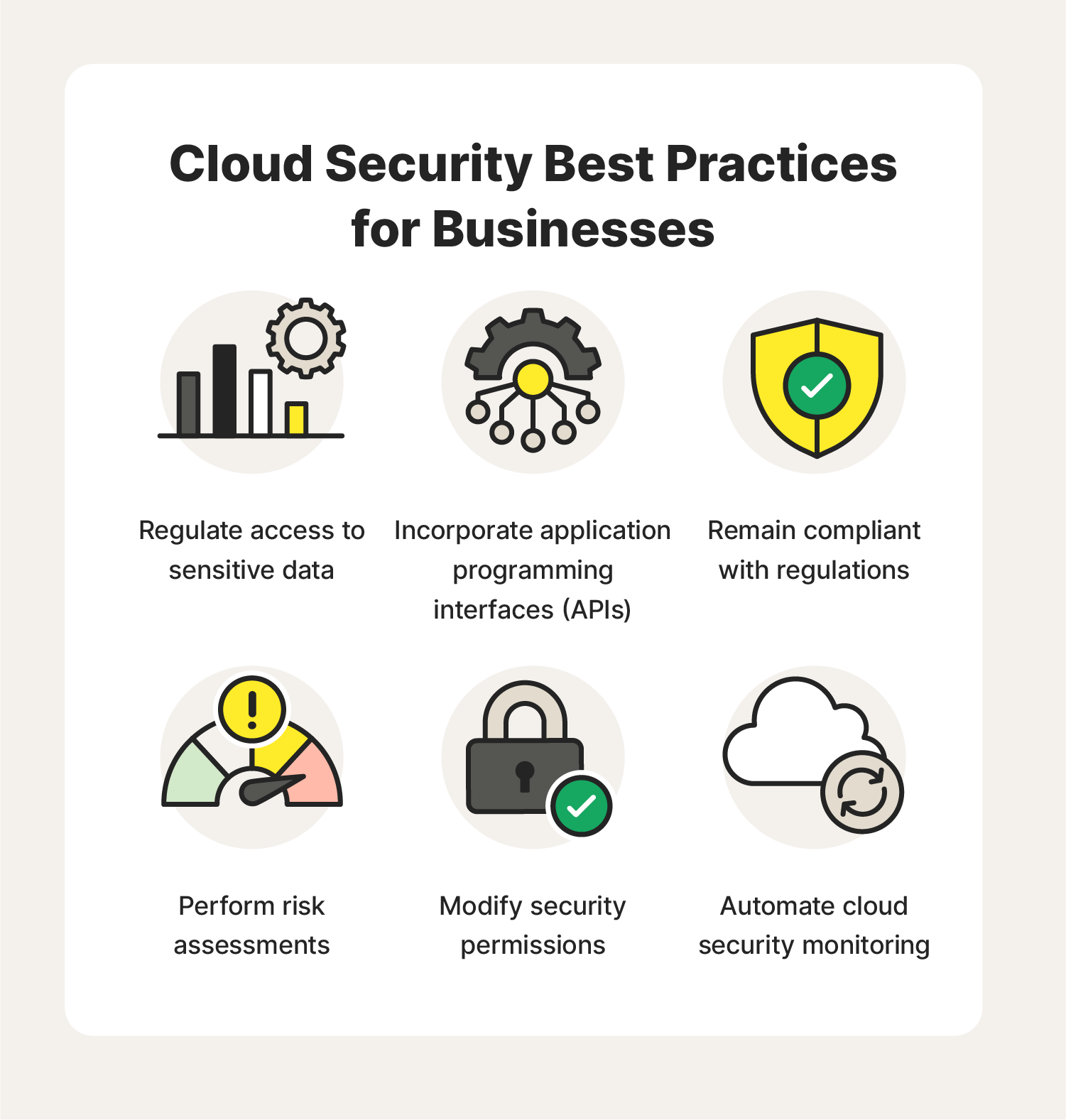
Cloud Security Threats Prevention Methods Best Practices 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to. Data breaches. data losses. attack surface. insecure apis. misconfiguration. restricted visibility of cloud usage. contract breaches with business partners. hijacking of accounts. data breaches transpire when nefarious actors manage to penetrate the system and gain unauthorized access to sensitive data. When choosing an msp in order to mitigate threats to the cloud tenant through the msp. organizations should select providers that comply with the security standards and practices important to the organization. in addition, organizations should audit msp accounts and operations in the environment, prioritizing privileged accounts and activities. Therefore, it is crucial to implement best practices to secure data in cloud services. 1. choose a reliable cloud service provider. choosing a reputable cloud service provider is the first step toward securing data. the provider should offer secure data storage, encryption, and access controls.

Cloud Security Threats Prevention Methods Best Practices When choosing an msp in order to mitigate threats to the cloud tenant through the msp. organizations should select providers that comply with the security standards and practices important to the organization. in addition, organizations should audit msp accounts and operations in the environment, prioritizing privileged accounts and activities. Therefore, it is crucial to implement best practices to secure data in cloud services. 1. choose a reliable cloud service provider. choosing a reputable cloud service provider is the first step toward securing data. the provider should offer secure data storage, encryption, and access controls.
What Is Cloud Security An Overview Best Practices Norton

Comments are closed.