Cloud Security Best Practices Protecting Your Data In The Cloud Be Learn Cloud

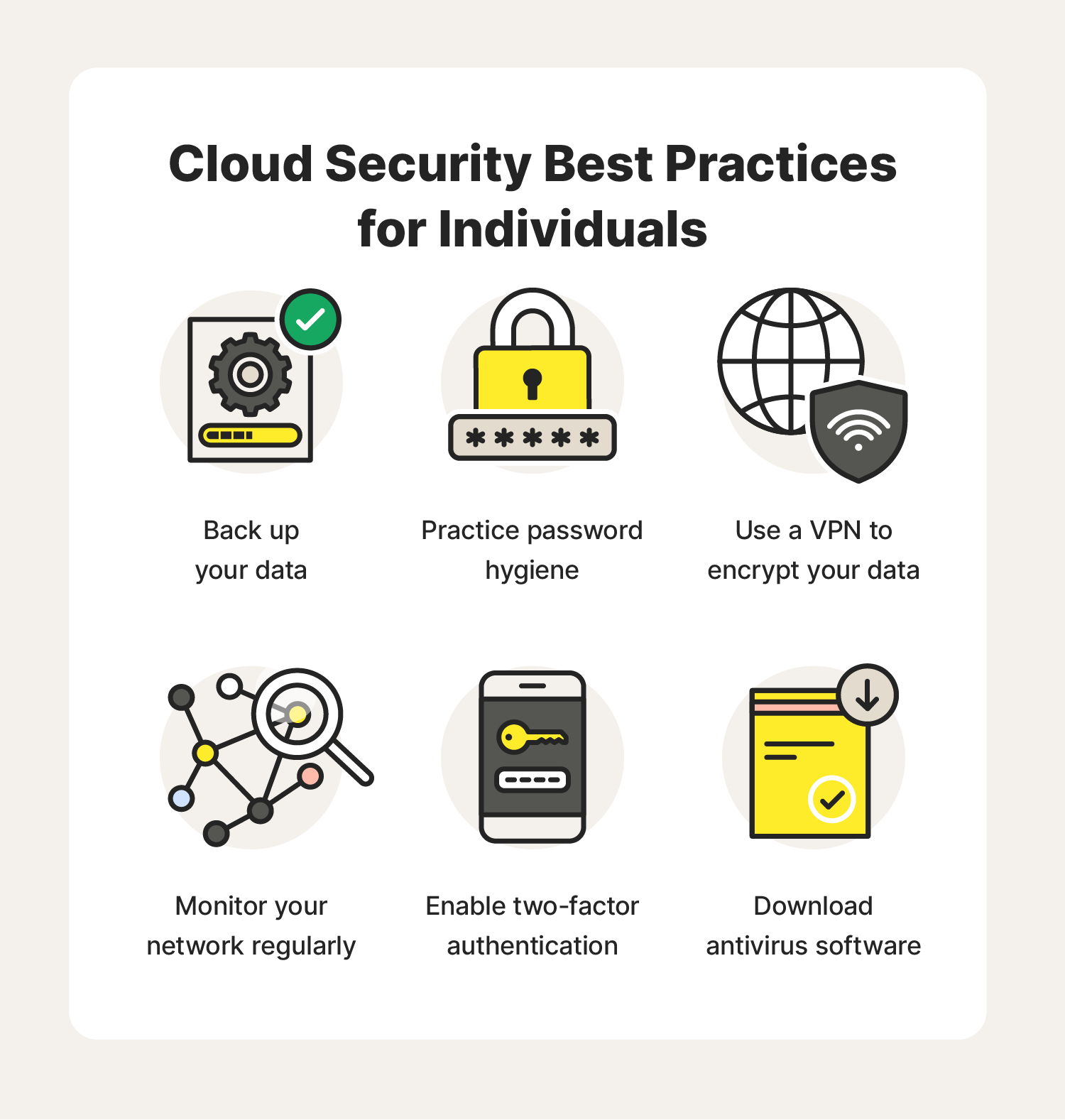
Infographic Best Practices For Securing The Cloud Therefore, it is crucial to implement best practices to secure data in cloud services. 1. choose a reliable cloud service provider. choosing a reputable cloud service provider is the first step toward securing data. the provider should offer secure data storage, encryption, and access controls. Secure the perimeter. monitor for misconfigurations. use identity and access management. enable security posture visibility. implement cloud security policies. secure your containers. perform vulnerability assessment and remediation. implement a zero trust approach. implement a cybersecurity training program.

Cloud Security Best Practices Protecting Your Data In The Cloud Be Learn Cloud Cloud security is the set of strategies and practices for protecting data and applications that are hosted in the cloud. like cyber security, cloud security is a very broad area, and it is never possible to prevent every variety of attack. however, a well designed cloud security strategy vastly reduces the risk of cyber attacks. Cloud security definition. cloud security is a discipline of cybersecurity focused on the protection of cloud computing systems. it involves a collection of technologies, policies, services, and security controls that protect an organization’s sensitive data, applications, and environments. cloud computing, commonly referred to as “the. The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to.

Data Security In Cloud Computing The Complete Guide The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 1. encrypt data at rest and in transit. protecting sensitive data is a top priority in cloud security. encrypting data at rest, or data stored in the cloud, is essential to prevent unauthorized access and data breaches. organizations should leverage cloud providers’ encryption services and implement proper key management practices to. In this article, we learn more about cloud native data security, cloud security challenges, and best practices for protecting your data in the cloud. an overview of cloud data security. cloud data security is a new and rapidly evolving security discipline designed to safeguard data, wherever it resides in the cloud. Cloud data security refers to the technologies and controls that discover, classify, and protect all data in the cloud to mitigate risks arising from data loss, misuse, breaches, and unauthorized access. this includes: detecting and classifying structured and unstructured data. implementing and monitoring access management controls at the file.
What Is Cloud Security An Overview Best Practices Norton In this article, we learn more about cloud native data security, cloud security challenges, and best practices for protecting your data in the cloud. an overview of cloud data security. cloud data security is a new and rapidly evolving security discipline designed to safeguard data, wherever it resides in the cloud. Cloud data security refers to the technologies and controls that discover, classify, and protect all data in the cloud to mitigate risks arising from data loss, misuse, breaches, and unauthorized access. this includes: detecting and classifying structured and unstructured data. implementing and monitoring access management controls at the file.

Comments are closed.