Cloud Security A Detailed Guide Ees Corporation
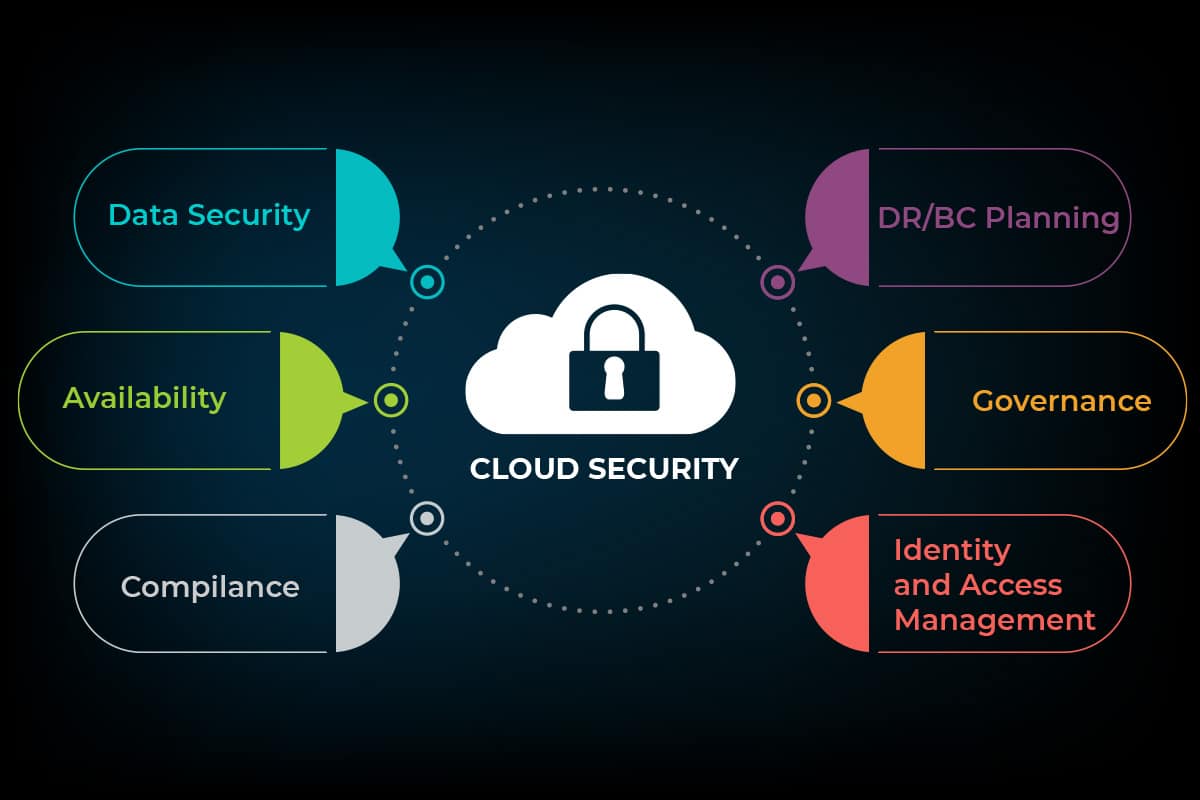
Cloud Security A Detailed Guide Ees Corporation Cloud security solutions. the best approach is “encryption” imposed on communications and sensitive data. end to end encryption of the data uploaded on the cloud is a must. always change the default settings to not give the hacker a front door access. always close the cloud storage bucket or else someone can open the urls easily. Customers and cloud computing providers must agree on security obligations to ensure responsibility. this approach is referred to as a shared responsibility model. it is the responsibility of the company to safeguard the it infrastructure and the data it contains, even if that infrastructure is operated and managed outside.
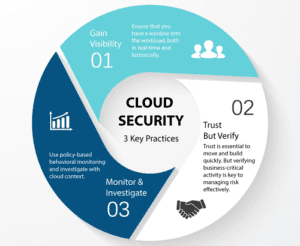
Cloud Security A Detailed Guide Ees Corporation This domain lays the foundational framework for the cloud security alliance (csa) security guidance. it covers the definitions, baseline terminologies, controls, deployment, and architectural models crucial for understanding cloud computing. learners will explore the transformative impact of cloud computing and its benefits when properly. Cloud readiness assessment: a comprehensive guide. with the day by day advancements of technology, more and more impactful and valuable methods are being introduced to ease operational labor. “cloud” or “cloud computing” is one of the advancements made in the modern era. a cloud is basically “all the stuff on the internet.”. The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. Secure the perimeter. monitor for misconfigurations. use identity and access management. enable security posture visibility. implement cloud security policies. secure your containers. perform vulnerability assessment and remediation. implement a zero trust approach. implement a cybersecurity training program.

Comments are closed.