Cloud Infrastructure Security 7 Best Practices For Cloud Data Protection Ekran System
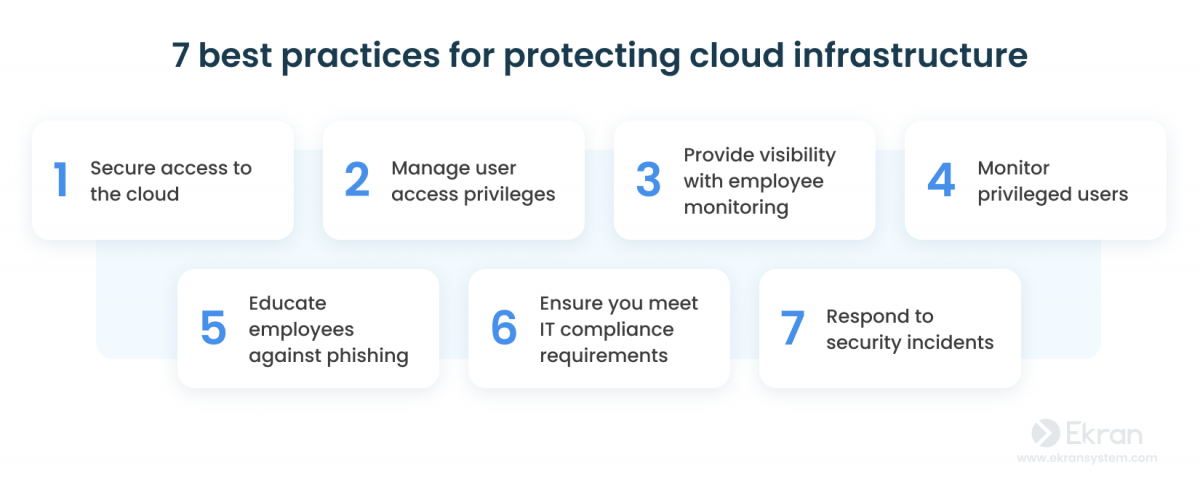
Cloud Infrastructure Security 7 Best Practices For Cloud Data Protection Ekran System Ekran system is a comprehensive irm platform that can help you protect your cloud infrastructure and sensitive data in numerous ways. access management. with ekran system, your security teams can restrict access to sensitive cloud resources based on user roles and permissions. more specifically, you’ll be able to:. Ekran system’s robust insider risk management capabilities, coupled with the advantages of its saas deployment model, help you secure your critical assets and maintain data integrity with utmost.
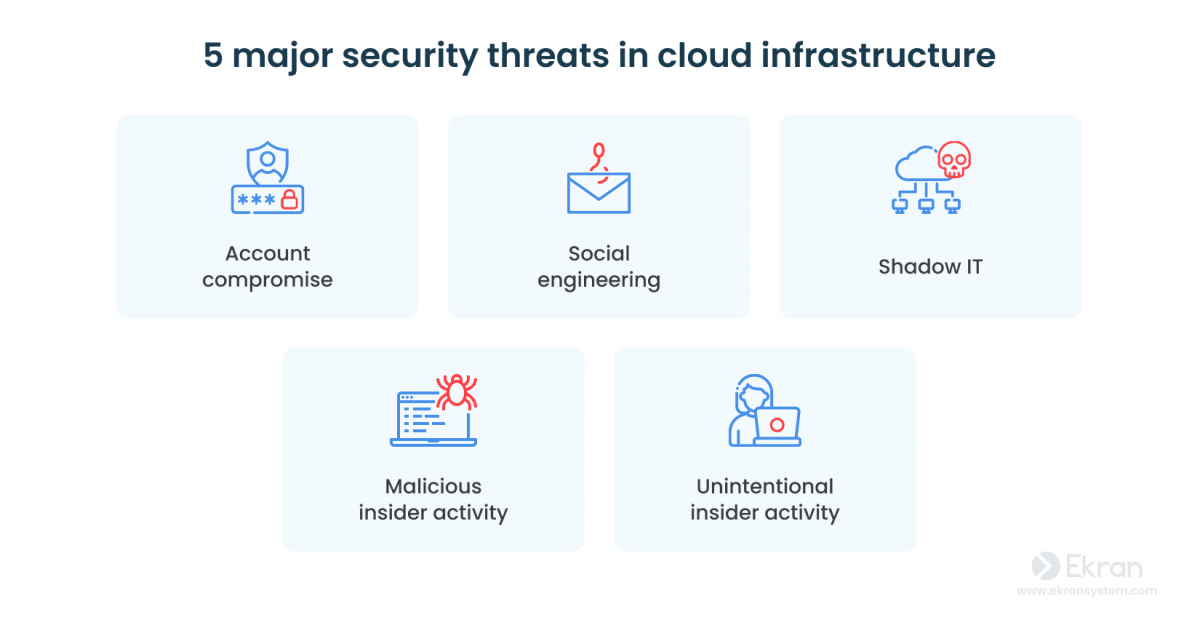
Cloud Infrastructure Security 7 Best Practices For Cloud Data Protection Ekran System Next, we’ll get into best practices that your organization can take on to effectively play its part in cloud data protection. 7 best practices for cloud data protection. when it comes to safeguarding sensitive information stored, processed, and transmitted in the cloud, an effective cloud data security strategy involves a blend of components. 7 cloud security best practices to protect sensitive data. cloud security combines different cybersecurity strategies, processes, and solutions. we’ve summarized the most efficient means of protecting your cloud computing environment in our seven cloud data security best practices: 1. secure access to the cloud. Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach. Enhancing information security. protecting important data in cloud computing means adjusting security measures to deal with higher risks presented by shared and distributed cloud storage solutions. this includes evaluating data ownership, ensuring compliant data management practices, and implementing robust security measures like encryption.
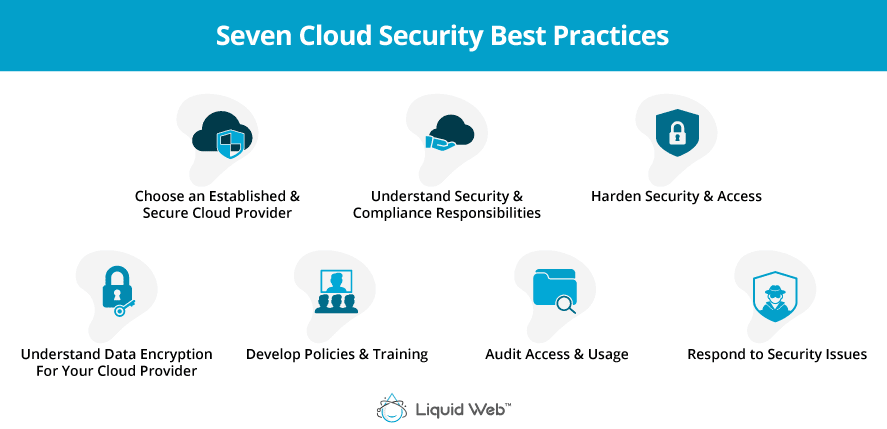
Cloud Security Best Practices 7 Things You Must Do Liquid Web Use log management and continuous monitoring. conduct penetration testing. encrypt your data. meet compliance requirements. implement an incident response plan. secure all applications. keep data security posture in mind. consolidate your cybersecurity solutions. leverage a cloud detection and response approach. Enhancing information security. protecting important data in cloud computing means adjusting security measures to deal with higher risks presented by shared and distributed cloud storage solutions. this includes evaluating data ownership, ensuring compliant data management practices, and implementing robust security measures like encryption. Cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: the cloud data protection and security strategy must also protect data of. Use our seven cloud security best practices as a checklist to protect your cloud infrastructure from potential cybersecurity incidents and secure your organization’s sensitive data. efficient.
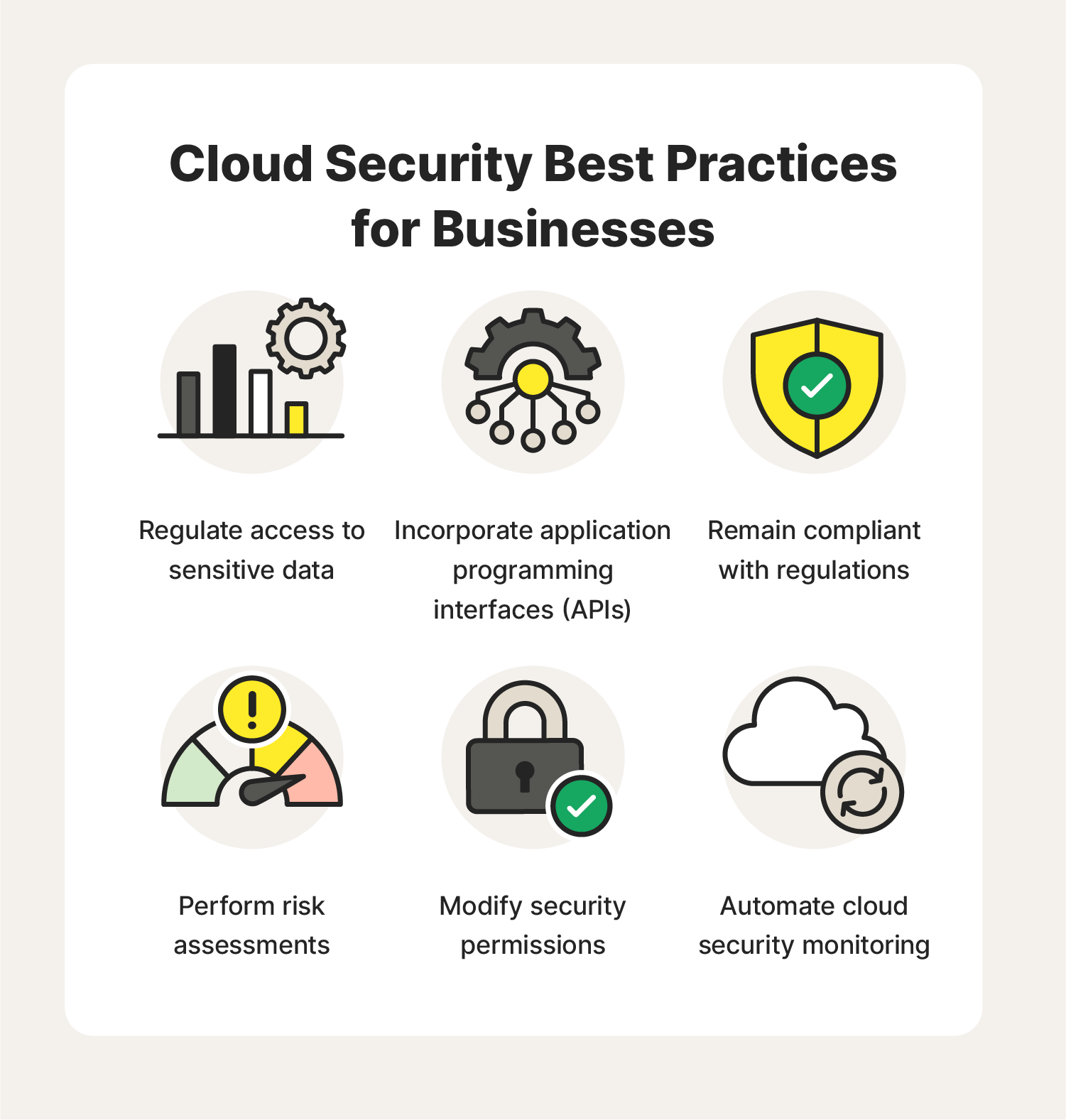
What Is Cloud Security An Overview Best Practices Norton Cloud data security refers to the technologies, policies, services and security controls that protect any type of data in the cloud from loss, leakage or misuse through breaches, exfiltration and unauthorized access. a robust cloud data security strategy should include: the cloud data protection and security strategy must also protect data of. Use our seven cloud security best practices as a checklist to protect your cloud infrastructure from potential cybersecurity incidents and secure your organization’s sensitive data. efficient.

Comments are closed.